Blueprint 7: "The Quantum Index" 🔑
Blueprint 7: "The Quantum Index" 🔑
1. The Mission Briefing: The Need for Instant Access
"Architect, searching through lists for data, even sorted ones, takes time. When a critical system needs clearance codes, it can't wait for a binary search. We need a way to access data instantly, as if by magic. The Labyrinth uses a protocol called Hashing to create a 'quantum index' that maps a key directly to its storage location, bypassing the need to search altogether."
When dealing with massive datasets, even a hyper-efficient O(log n) search can be too slow. We need a system that aims for O(1)—Constant Time—where the size of the dataset has virtually no impact on the time it takes to find a specific item. This seems impossible, but Hashing makes it a reality.
2. The Analogy: The Coat Check
A Hash Map (also known as a Hash Table, Dictionary, or Object in many languages) is like a high-tech coat check room.
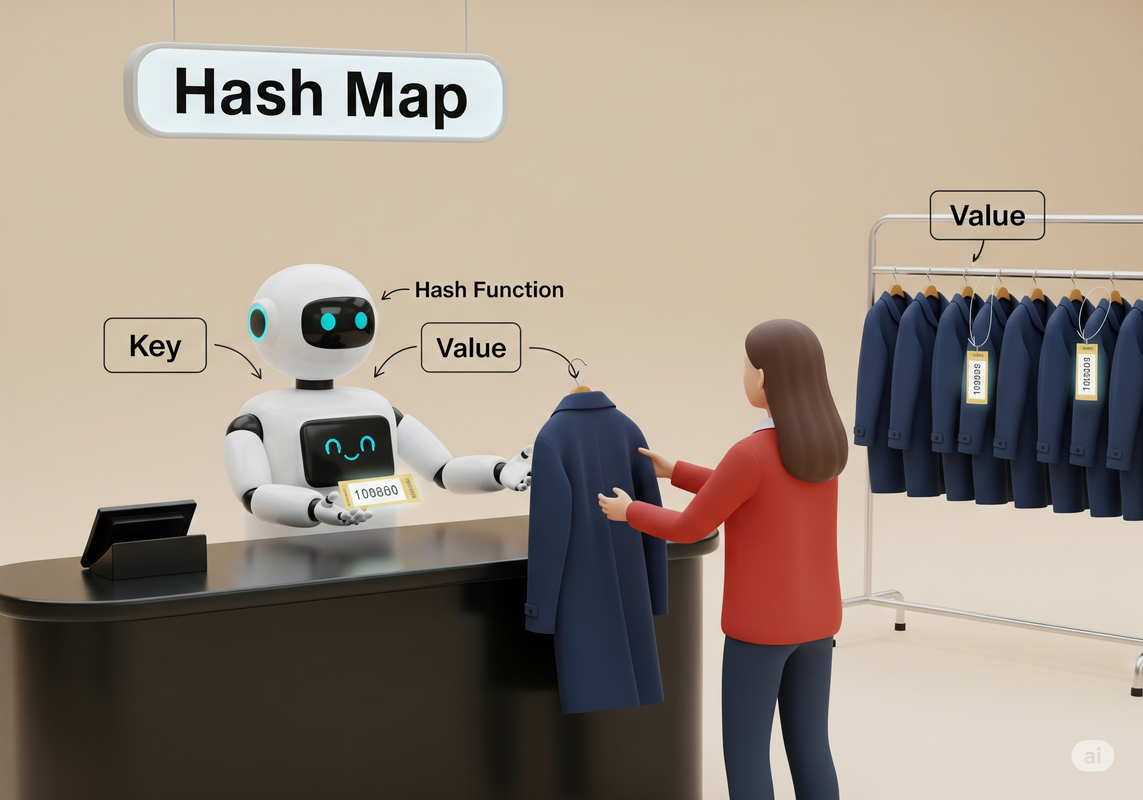
You give the attendant your coat (the value), and they give you a unique ticket number (the key). To get your coat back, you don't need to search through all the other coats. You just hand them your ticket, and they retrieve it instantly.
The "magic" is the system the attendant uses. This system is the hash function.
3. The Engine: The Hash Function
A hash function is the core of any hashing system. It's a special algorithm that takes an input (your key) and converts it into a fixed-size number, which we then use as an index in an array.
The Goal: To take a key of any size (like the string "alpha-7") and turn it into an integer that corresponds to a slot in our underlying array.
The Properties of a Good Hash Function:
- Fast: It must be incredibly quick to compute.
- Deterministic: The same key must always produce the same output index. "alpha-7" must always map to index 4.
- Uniform Distribution: It should spread keys evenly across the array slots to avoid clustering.
4. The Inevitable Problem: Collisions
What happens if the coat check attendant\'s system tells them to hang two different coats on the same hook? This is a collision. It happens when our hash function generates the same index for two or more different keys. Since we can\'t store two items in the same array slot, we need a strategy to handle this.
5. The Solution: Separate Chaining
The most common way to handle collisions is a technique called Separate Chaining. Instead of a single hook, each spot in the coat check room has a short chain. If two coats map to the same spot (e.g., hook #4), the attendant hangs the first coat on the hook, and the second coat on the first link of the chain. In our data structure, the "chain" is a Linked List. Our underlying storage is an array of linked lists (often called buckets).
Interactive Hash Table
This simulation visualizes a hash table using Linear Probing to handle collisions. Enter a number and click Insert or Search to see how it works. The hash function is key % 11.
Enter a key and choose an operation.
6. Implementing a Hash Map
Nearly all modern languages provide a powerful, highly-optimized, built-in Hash Map.
# Python: Dictionaries
crew_roster = {}
crew_roster['id-007'] = {'name': 'James', 'clearance': 'Alpha'}
crew_roster['id-009'] = {'name': 'Eva', 'clearance': 'Gamma'}
print(crew_roster.get('id-007'))7. The Time Complexity Explained
- Best Case: O(1) - The key hashes to an empty or small bucket. You find the item instantly.
- Worst Case: O(n) - A terrible hash function puts all n items into the same bucket. Your hash map effectively becomes a single, slow linked list, and you have to do a linear search.
- Average Case: O(1) - With a good hash function that distributes keys evenly, collisions are rare, and the linked lists (chains) remain very short. Therefore, on average, the time to find, insert, or delete an item is constant. This is why hash maps are so powerful and widely used.
8. Common Use Cases
Database Indexing, Caching, Compilers (Symbol Tables).
9. Blueprint Summary
Concepts Unlocked: Hashing, Hash Maps (Objects/Dictionaries), Key-Value Pairs, Hash Functions, Collisions, Separate Chaining, Average-Case O(1) operations.